Russian banks propping up Moscow’s invasion of Ukraine. A Chinese paramilitary group linked to human rights abuses. And a company owned by an accused Lithuanian drug trafficker.
These are some of the dozens of U.S.-sanctioned organizations that have offered apps in the Apple App Store, a Tech Transparency Project (TTP) investigation found, raising questions about the iPhone giant’s dealings with entities deemed a threat to U.S. national security.
TTP identified 52 apps in the App Store with direct connections to Russian, Chinese, and other companies that are under U.S. economic sanctions enforced by the U.S. Treasury Department. All of the apps listed a developer, seller, copyright holder, or other information on their App Store page that matched with a U.S.-sanctioned entity.
The investigation found that the Google Play Store had a similar problem, though at a lower level. Google’s app store hosted 18 apps connected to U.S.-sanctioned organizations, roughly a third of the number identified in the Apple App Store.
Apple and Google may be violating Treasury Department sanctions by simply hosting these apps. Because both companies charge a fee to app developers, they may also be engaging in financial transactions with sanctioned organizations in some cases.
These findings raise questions about how thoroughly Apple and Google vet the apps in their app stores. Both companies say they comply with U.S. sanctions, and Apple says it hold apps to the “highest standards” of security. But the apps identified by TTP showed obvious signs of their connection to sanctioned companies.
Apple has been fined before by the U.S. government for failing to guard against sanctions violations in the App Store, over a case involving an app linked to a sanctioned Slovenian drug trafficker in 2019. As part of a settlement with the Treasury Department, Apple promised to take steps to improve its sanctions screening tools. But TTP’s investigation suggests Apple is falling short six years later.
Apple declined to comment or respond to questions but asked for the list of apps, which TTP provided. Shortly after that, 24 of the apps disappeared from the App Store, leaving 11 available. (Another 17 apps were removed during the course of TTP’s research, though many of them had been available for months in the App Store after sanctions came into force.)
Google also asked for the list of apps and removed 17 of the 18 apps identified in the Google Play Store. Google declined to answer questions but provided a statement saying it is “committed to compliance with applicable sanctions and trade compliance laws,” adding, “If we find that an account violates our Terms of Service, we take appropriate action.”
Methodology and background
To investigate whether sanctioned individuals or organizations have a presence in the Apple and Google app stores, TTP used a combination of automated and manual searches.
For the automated search, TTP focused on what the U.S. Treasury Department calls Specially Designated Nationals (SDNs). These are U.S.-sanctioned individuals, groups, and companies whose assets are blocked. “U.S. persons,” a category that includes U.S. citizens and permanent residents as well as U.S.-incorporated entities, are prohibited from engaging in transactions with them without authorization.
In July 2025, TTP downloaded the full list of SDNs from the Treasury Department’s Office of Foreign Assets Control (OFAC) website and removed business suffixes (like “Inc.,” LLC,” and their foreign equivalents). Researchers then used a simple Python script to search for each SDN name on the app store domains apps.apple.com and play.google.com, using the Google Custom Search API. The program recorded results in a spreadsheet, which our team reviewed to verify matches. TTP supplemented this automated process with a series of manual searches for SDNs in the app stores, including in languages like Russian, Chinese, and Arabic. The research was conducted through mid-November 2025.
Through this process, TTP identified 70 apps that matched with SDNs, 52 in the Apple App Store and 18 in the Google Play Store. Six of the SDNs had apps in both app stores.
TTP’s analysis showed that Apple approved 17 of the apps after the companies behind them were already under U.S. sanctions. Apple also allowed updates to 27 of the apps connected to sanctioned companies despite saying it reviews all app updates. Google allowed updates to 11 of the apps despite saying it runs safety checks before apps are updated.
These findings point to potential sanctions violations by Apple and Google. OFAC regulations prohibit transactions with sanctioned entities including the “making of any contribution or provision of funds, goods, or services by, to, or for the benefit of any blocked person and the receipt of any contribution or provision of funds, goods, or services from any such person.”
By giving these apps a platform and making them available to consumers, Apple and Google are contributing a service to them. The two companies may also be conducting financial transactions with the apps that list a sanctioned company as their developer. That’s because Apple and Google both charge a fee to app developers. Apple charges an annual fee of $99 USD ($299 for enterprise customers), while Google charges a $25 one-time fee. (One SDN-connected app in the Apple App Store also indicated it offers in-app purchases, in which Apple takes a cut.)
OFAC has warned that sanctions violations can result in civil or criminal penalties and that civil liability may apply even in cases where the U.S. party “did not know or have reason to know” they were engaging in a prohibited transaction.
Apple has direct experience with this issue, having reached a settlement with OFAC in 2019 for hosting, selling and facilitating the transfer of software for the apps of a Slovenian software company called SIS d.o.o. The company and its owner had been sanctioned under Foreign Narcotics Kingpin Sanctions Regulations for their role in an international steroid trafficking operation.
Apple agreed to pay a fine of $466,912 in that case. According to OFAC, the government could have imposed a penalty as high as $74 million but reduced the amount due to the fact that Apple voluntarily disclosed the issue, the case was non-egregious, and the company promised to take steps to improve its sanctions screening process.
Per OFAC’s notice, Apple attributed its failure to identify the Slovenian company to a capitalization mix-up and pledged to reconfigure its sanctions screening tool to “capture spelling and capitalization variations and to account for country-specific business suffixes.” The company also promised to increase the role of its sanctions compliance senior manager; conduct an annual review of its sanctions screening tool; and do mandatory training for employees on sanctions regulations, among other measures.
But TTP’s investigation found that Apple failed to identify sanctioned organizations whose names differed only slightly from how they appear in OFAC’s public database, in their punctuation, spacing between words, or abbreviation of business suffixes. In several cases, Apple failed to identify a sanctioned organization that exactly matched the way an organization was listed in OFAC’s database.
The U.S. often issues what are called general licenses carving out exemptions in sanctions for certain kinds of humanitarian or other activities. TTP examined the general licenses for sanctions applying to the companies mentioned in this report, including those related to Russia, Belarus, China, Venezuela, and Yemen, as well as the Global Magnitsky Act and non-proliferation. None of the general licenses appeared to allow for provision of digital services such as hosting apps in an app store or charging app developer fees.
TTP was not able to determine if Apple or Google sought specific licenses to do business with any of the SDNs identified in this report.
Below, we give details on some of the apps identified in the investigation. A full list follows at the bottom of this report.
Apple App Store
Apple says it offers “a highly curated App Store where every app is reviewed by experts” and complies with sanctions regulations in all countries in which it operates. The company warns it will terminate agreements with developers who are directly or indirectly controlled by sanctioned entities or create apps for sanctioned entities.
But TTP identified 52 apps in the Apple App Store that showed a direct connection to U.S.-sanctioned organizations.
Seven of the apps listed a developer, seller, copyright holder, or other organization on their App Store page that exactly matched the spelling of an SDN on OFAC’s sanctions list. Another 25 apps had information that matched a sanctioned organization but with slightly different punctuation, spacing between words, or business suffix, or were written in a non-English language.
More than half of the apps (29) were for sanctioned Russian companies, and many of these were banking or mobile payment apps.
For example, TTP identified four apps connected to the Russian commercial bank Ural FD, which has been under Treasury Department sanctions since November 2024. The apps, which are available in the U.S. and Russian app stores, are:
- Урал ФД СБП (Ural FD SBP)
- Урал ФД для смартфона (Ural FD for Smartphones)
- Клюква Mobile (Cranberry Mobile)
- Дом.ру банк (Dom.ru bank)
The first two apps listed their developer and seller, in English, as Ural FD KB OAO. “OAO” is the Russian corporate suffix for an open joint stock company, which is similar to how the bank is described in the OFAC database. Both apps linked to a support page on the domain uralfd.ru, which OFAC identifies as belonging to Ural FD.
The “SBP” in the first app’s name appears to refer to the Russian central bank’s Faster Payments System for interbank transfers using a mobile phone number. The app’s description section says it provides “SBP functionality for organizations/entrepreneurs.”
The other two apps listed their seller as AKB Ural FD, PAO and described themselves as an “official mobile app” of Ural FD. The Клюква Mobile app description section said “Клюква” (Cranberry) is a brand of Ural FD, and the Дом.ру банк (Dom.ru bank) app linked to a privacy policy on uralfd.ru.
According to app analytics firm AppMagic, three of the Ural FD apps have each been downloaded more than 20,000 times, the vast majority of times in Russia.
The Treasury Department sanctions against Ural FD were aimed at curtailing Russia’s use of the international financial system to fund its war in Ukraine.
TTP identified four apps connected to the Russian bank Ural FD, which is under U.S. government sanctions.
TTP identified four apps connected to the Russian bank Ural FD, which is under U.S. government sanctions.
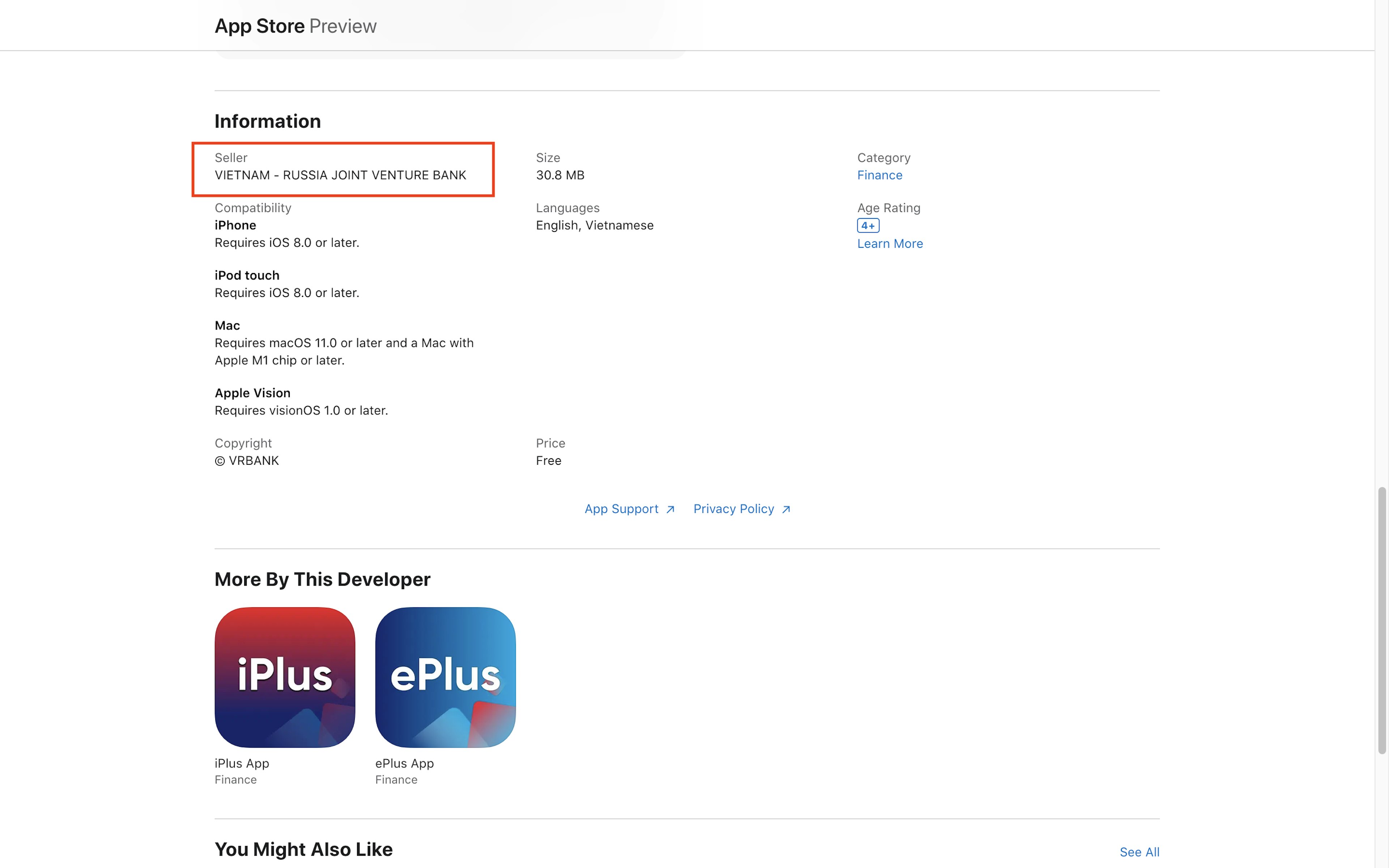
Another three mobile banking apps—mPAY VRB, iPlus App, and ePlus App—listed their seller as “VIETNAM - RUSSIA JOINT VENTURE BANK.” They appeared in both the U.S. and Russian App Stores.
The U.S. Treasury Department announced sanctions against Vietnam-Russia Joint Venture Bank and its parent company, Russia’s VTB Bank, in February 2022. According to the announcement, VTB Bank is Russia’s second largest financial institution and majority-owned by the Russian government.
OFAC’s public database clearly lists VIETNAM-RUSSIA JOINT VENTURE BANK as a Specially Designated national subject to economic sanctions. The apps spelled the name with a slight variation—putting an extra space on either side of the dash between “RUSSIA” and “VIETNAM”—but otherwise it was exactly the same as the OFAC listing.
The first app, mPAY VRB, also named Vietnam-Russia Joint Venture Bank in its description section, and linked to app support and privacy policy pages on vrbank.com.vn, a domain that OFAC says is associated with the bank.
Another three apps were connected the Vietnam-Russia Joint Venture Bank, which is under U.S. sanctions.
Another three apps were connected the Vietnam-Russia Joint Venture Bank, which is under U.S. sanctions.
It is not clear why Apple’s review process missed these Russian banks. Since Moscow’s invasion of Ukraine in 2022, Apple has removed apps for a number of U.S.-sanctioned Russian banks and limited access to banking and payment services for Russian users, drawing the ire of Russian antitrust regulators. But TTP’s findings suggest that Apple is still allowing some sanctioned Russian banks to have a presence in its App Store, undermining the U.S. effort to put pressure on Russia’s financial sector.
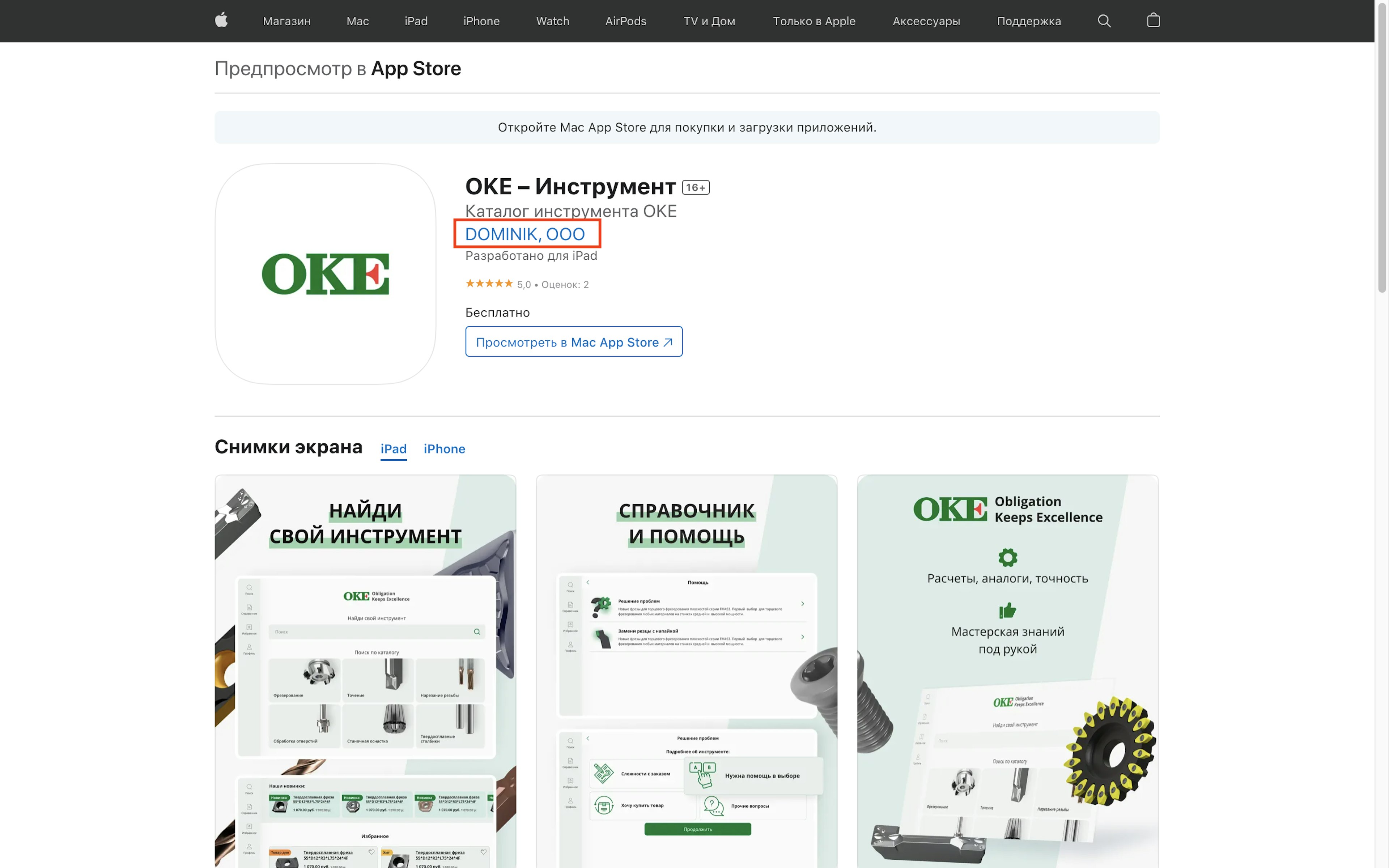
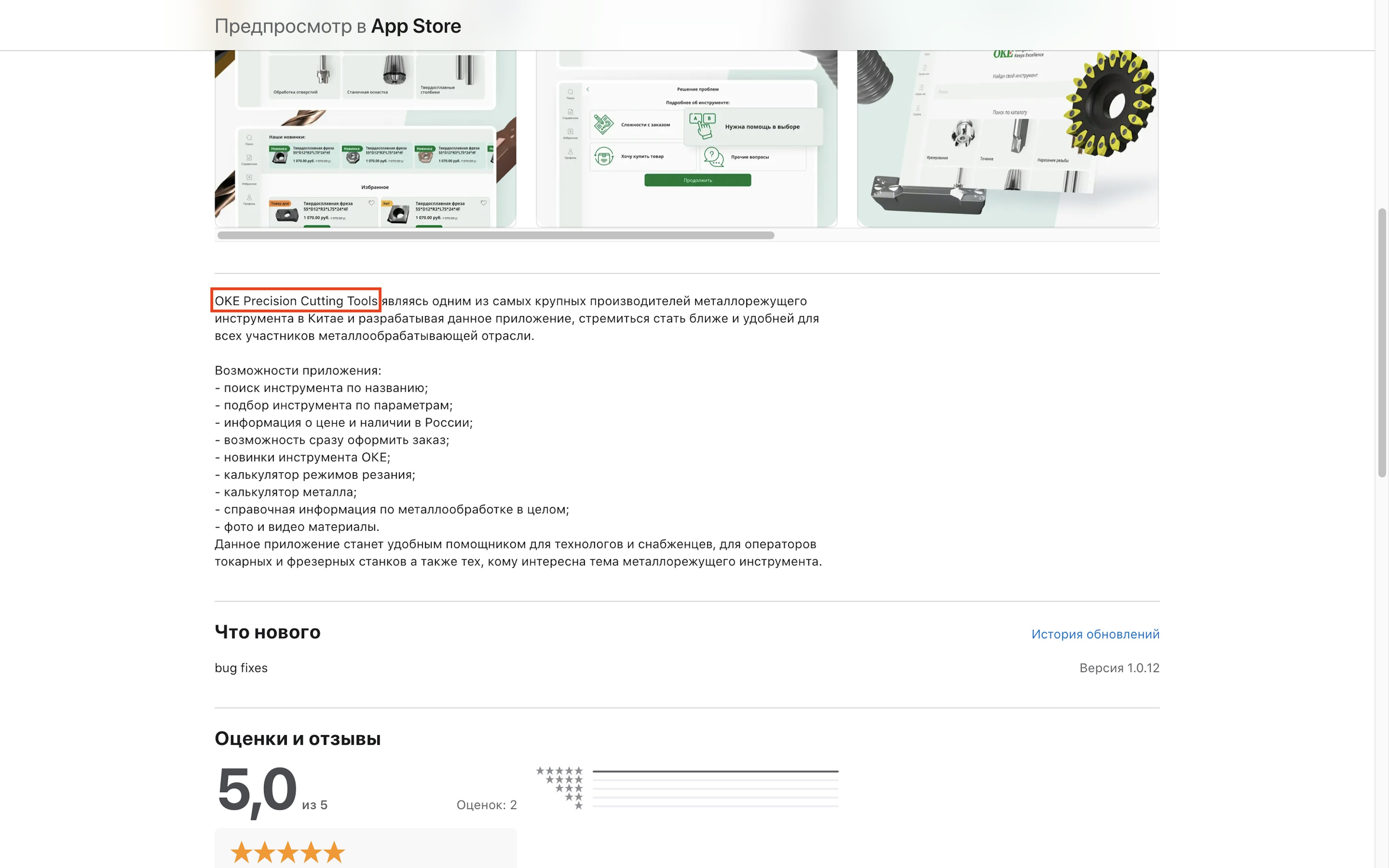
Another app identified by TTP, OKE-Инструмент (Russian for “OKE-Tool”), which was available in the Russian App Store, offered precision cutting tools for purchase.
The app gave its developer as DOMINIK OOO and named another company, OKE Precision Cutting Tools, in its description section. The U.S. announced sanctions against both companies in January 2025 as part of an effort to disrupt Russia’s military-industrial base supporting the war in Ukraine.
OFAC identifies the first company as OBSHCHESTVO S OGRANICHENNOI OTVETSTVENNOSTYU DOMINIK, putting the Russian term for Limited Liability Company, which is abbreviated as OOO, before “DOMINIK.” The app developer name had the terms in the reverse order.
According to the U.S. sanctions announcement, Dominik is an industrial cutting machine operation that has supplied Russian companies making rocket launchers and other weapons for use against Ukraine. It identifies China-based OKE Precision Cutting Tools as a supplier to Dominik, saying it transferred $7 million worth of manufacturing items to Dominik between 2023 and 2024.
Both Dominik and OKE Precision Cutting Tools are listed as SDNs in OFAC’s public database.
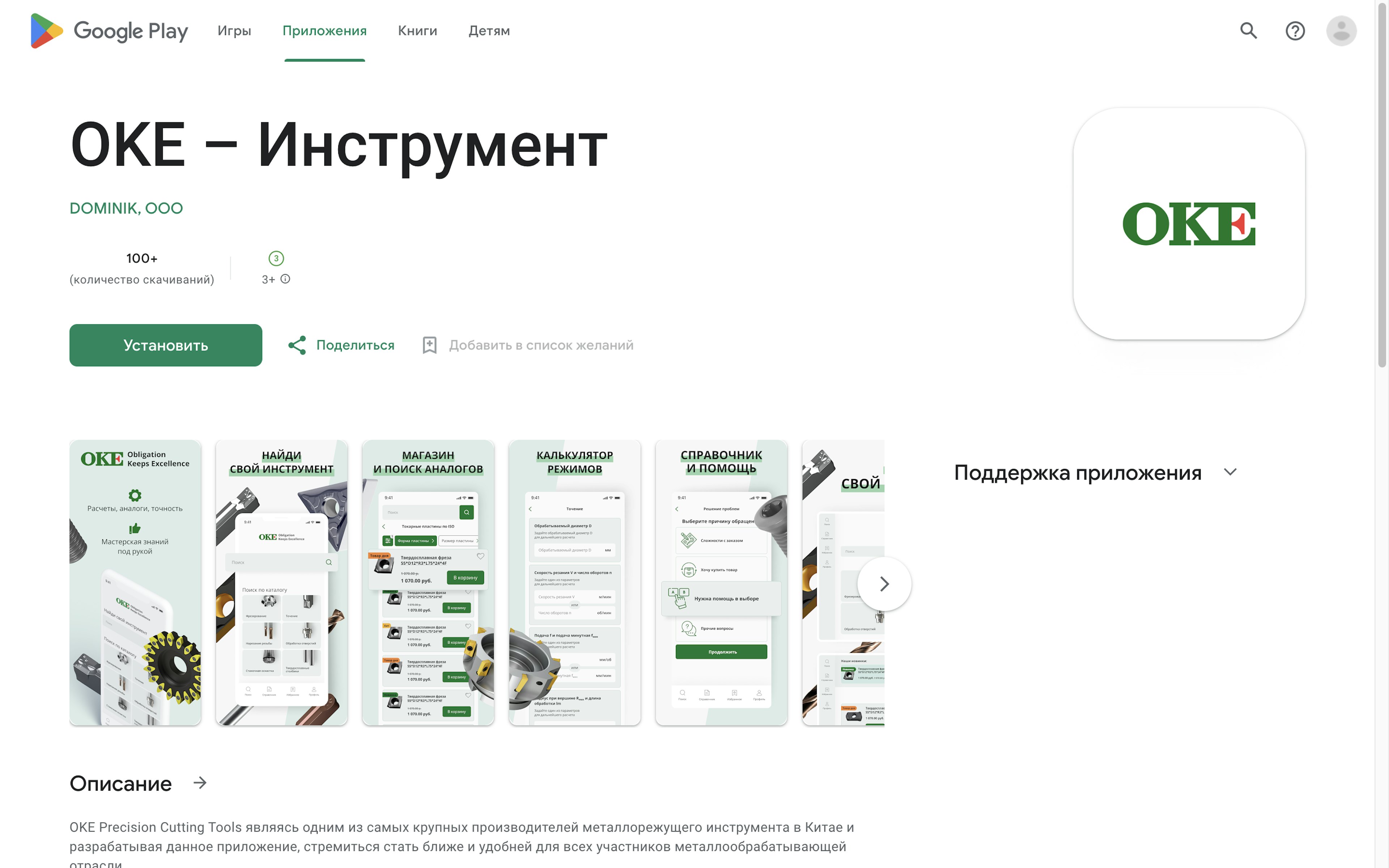
The app was also available in the Google Play Store.
This app for precision cutting tools listed a U.S.-sanctioned Russian company as its developer.
This app for precision cutting tools listed a U.S.-sanctioned Russian company as its developer.
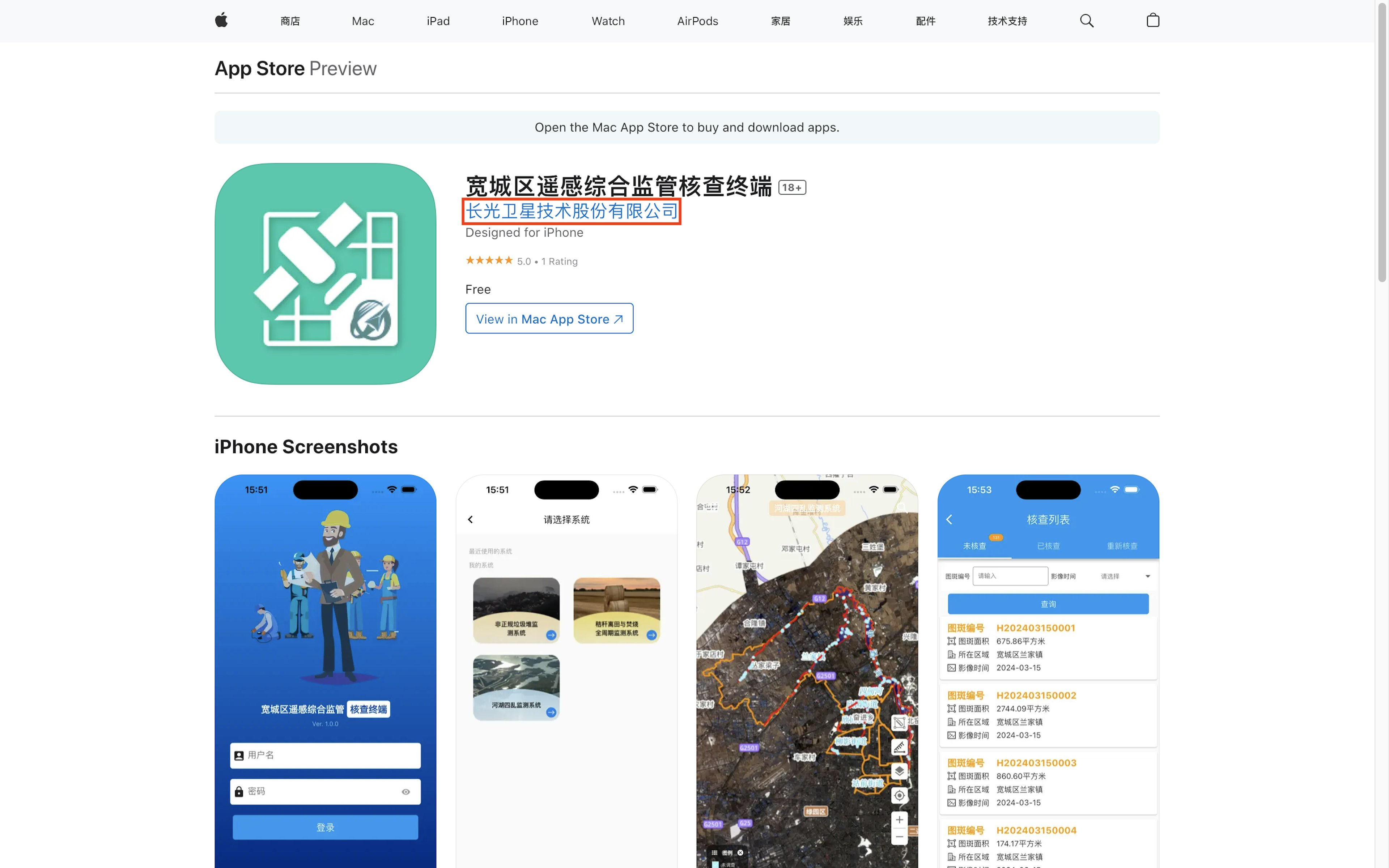
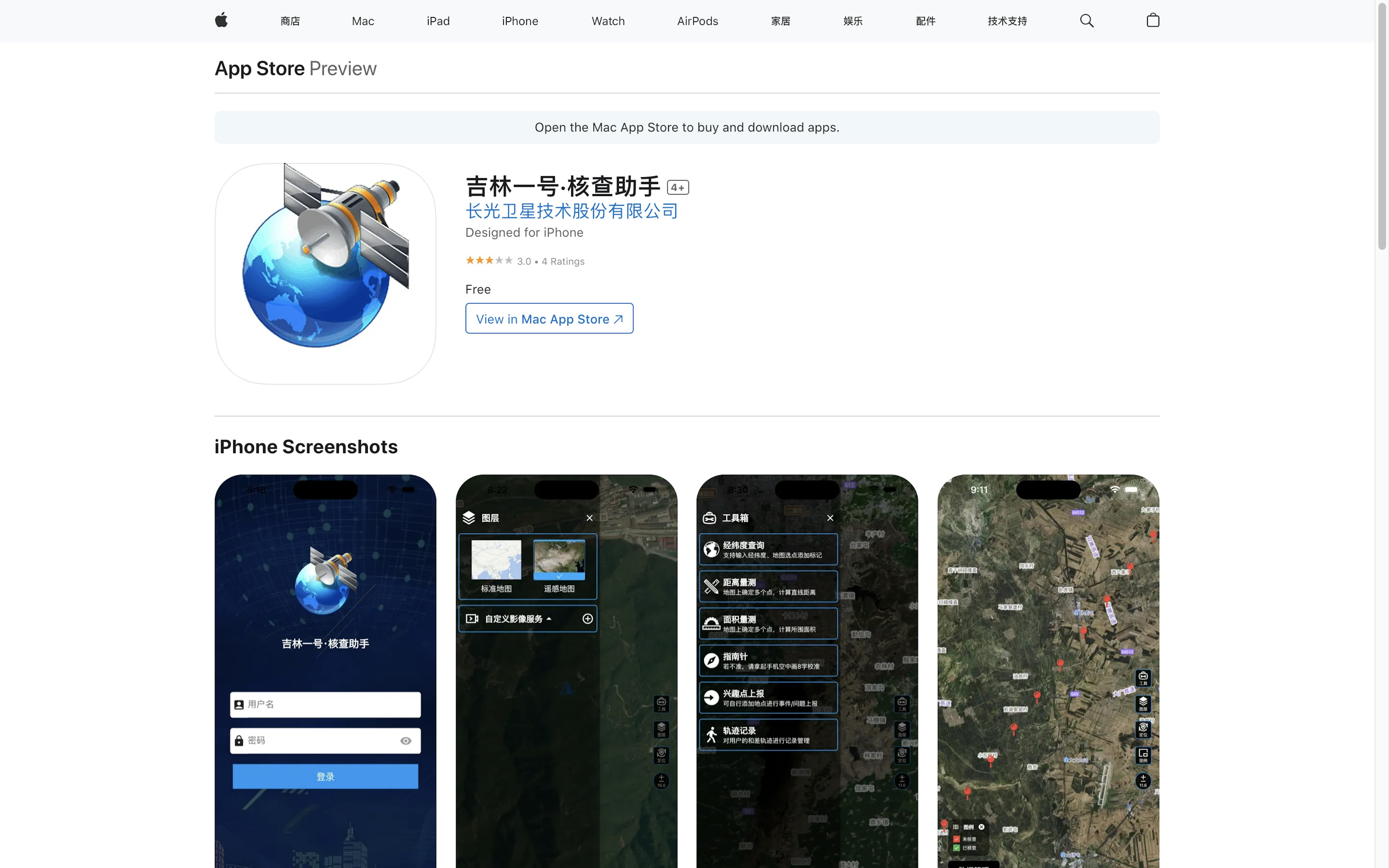
The investigation identified another four apps that listed their developer, in Chinese, as Chang Guang Satellite Technology Co., Ltd. They were all available in Apple’s China App Store:
- 吉林一号网 (Jilin No. 1 Network)
- 吉林一号·核查助手 (Jilin No. 1 Verification Assistant)
- 宽城区遥感综合监管核查终端 (Kuancheng District Remote Sensing Comprehensive Supervision and Verification Terminal)
- 共生地球 (Symbiotic Earth)
The U.S. Treasury Department announced sanctions on Chang Guang Satellite Technology Co., Ltd., in December 2023, saying the China-based company provided high-resolution satellite imagery to the Wagner Group, the Russian private military company that has conducted operations in Ukraine. The Wagner Group is itself under U.S. sanctions. (The group’s former leader, Yevgeny Prigozhin, led a brief mutiny against the Kremlin and was killed in a plane crash in August 2023.)
The developer name on these apps, when translated into English, exactly matches the listing in OFAC’s public database. The apps also listed Chang Guang Satellite Technology Co., Ltd., as their provider and copyright holder.
TTP identified another four apps that listed their developer, in Chinese, as Chang Guang Satellite Technology Co., Ltd.
TTP identified another four apps that listed their developer, in Chinese, as Chang Guang Satellite Technology Co., Ltd.
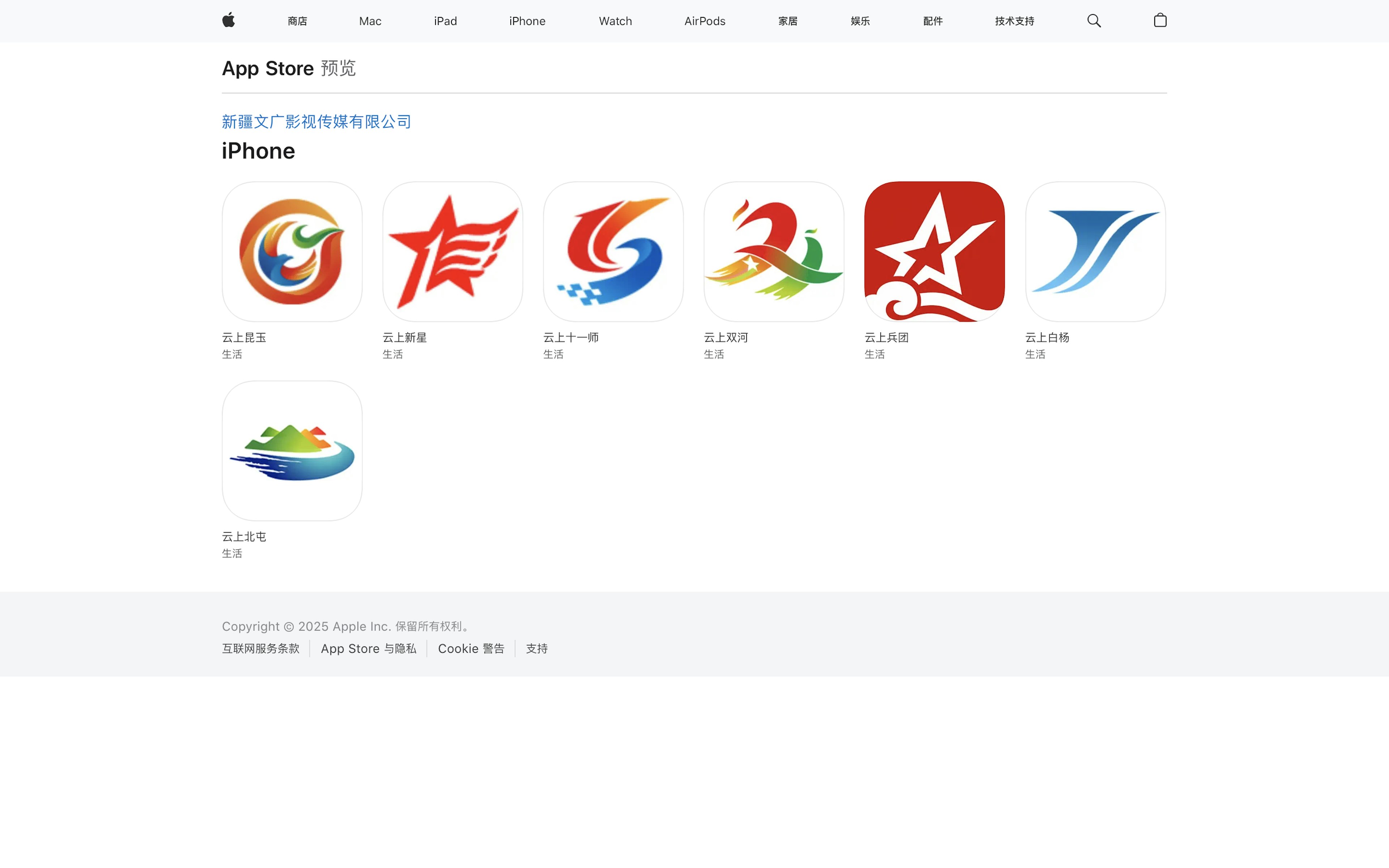
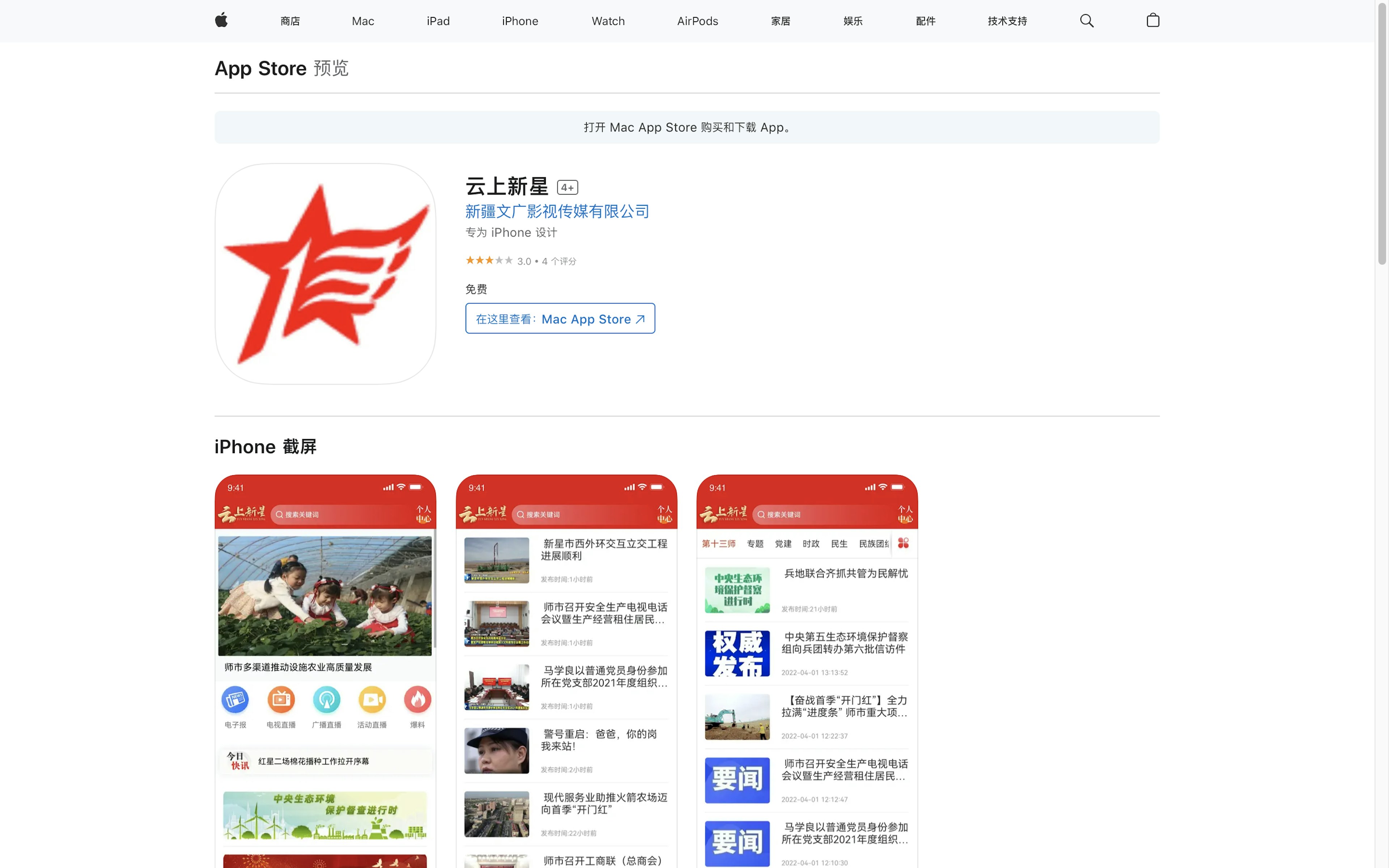
The China Apple App Store also hosted seven apps that listed their copyright holder as 新疆生产建设兵团文广传媒集团有限公司. That translates as Xinjiang Production and Construction Corps Media Group Co., Ltd.
The Xinjiang Production and Construction Corps (XPCC) is a Chinese paramilitary organization sanctioned by the U.S. for its role in human rights abuses against Muslim ethnic Uyghurs in China’s northwestern Xinjiang region.
The apps were all multi-purpose, distributing official information and providing ways to access government services. (XPCC divisions operate as quasi-governmental entities and administer large swathes of land within Xinjiang.)
Six of the apps covered specific regions of Xinjiang or divisions of the XPCC. The seventh app, 云上兵团 (“Corps in the Cloud”), pertained to the entire XPCC. It was the subject of Chinese state TV segment upon its launch in 2021.
Two of the apps, covering the 13th and 14th Divisions of the XPCC, had nearly identical descriptions, indicating they play a role in Chinese Communist Party propaganda. The descriptions stated that the apps are designed to “comprehensively, accurately, and timely disseminate the Party lines, principles, and policies, fully leveraging its role as the voice of the Party and the government.”
Chinese corporate records confirm that the copyright holder as well as the app’s listed developer 新疆生产建设兵团文广传媒集团有限公司 (Xinjiang SMG Television Media Co., Ltd.) are XPCC subsidiaries.
TTP identified one other app that gave Xinjiang SMG Television Media Co., Ltd. as its provider and linked to a privacy policy indicating it is a product of the 7th Division of the Xinjiang Production and Construction Corps.
The U.S. Treasury Department announced sanctions against the XPCC in July 2020 over its “connection to serious human rights abuse against ethnic minorities in Xinjiang, which reportedly include mass arbitrary detention and severe physical abuse, among other serious abuses targeting Uyghurs.”
OFAC’s public database identifies the organization as an SDN.
The Apple App Store in China had another cluster of apps for the Xinjiang Production and Construction Corps (XPCC), a Chinese paramilitary organization sanctioned over its role in human rights abuses against Muslim ethnic Uyghurs.
The Apple App Store in China had another cluster of apps for the Xinjiang Production and Construction Corps (XPCC), a Chinese paramilitary organization sanctioned over its role in human rights abuses against Muslim ethnic Uyghurs.
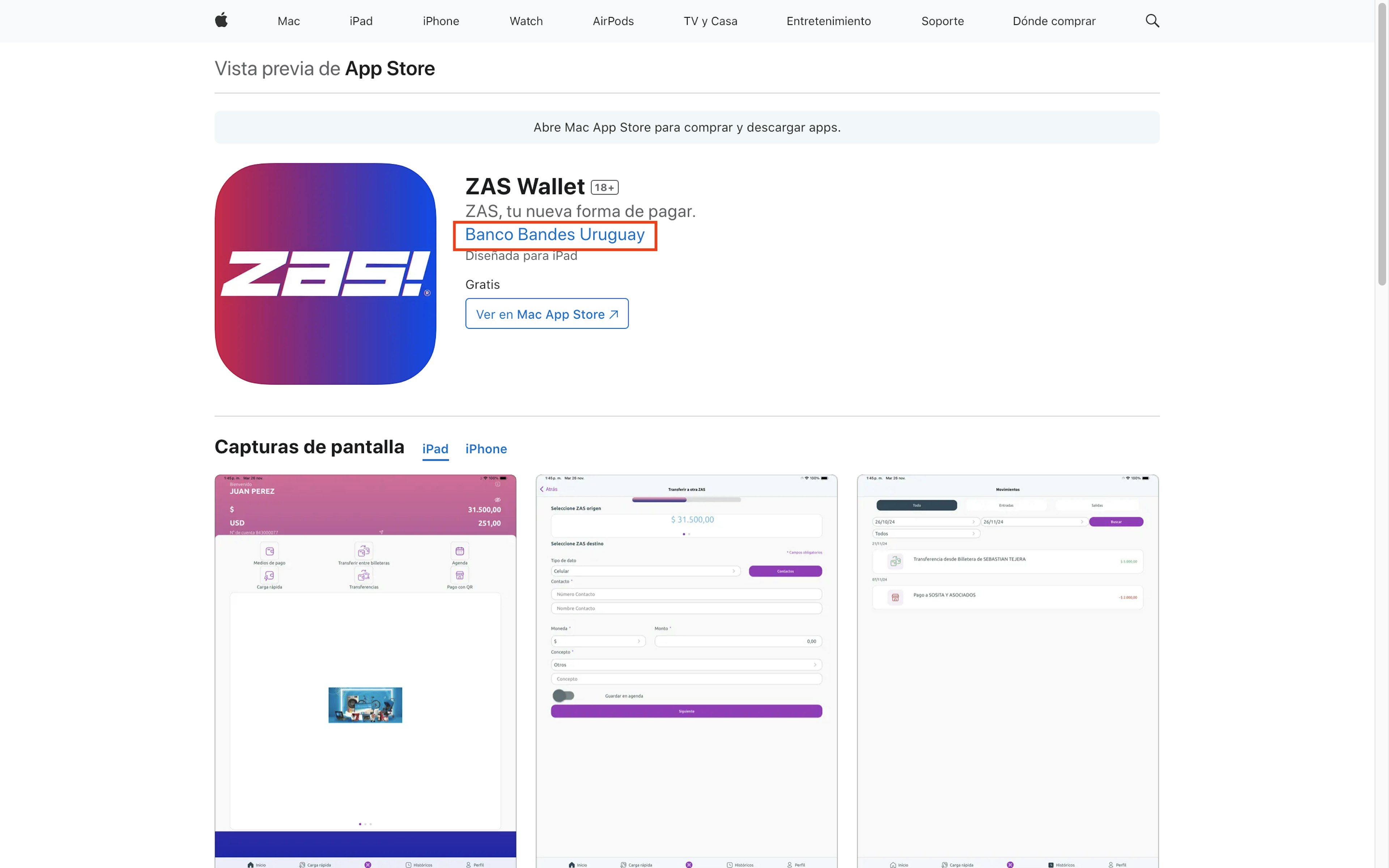
Two apps in the Uruguay version of the Apple App Store—ZAS Wallet for mobile payments and eBandes for mobile banking—listed their developer as Banco Bandes Uruguay.
The U.S. Treasury Department announced sanctions against Banco Bandes Uruguay in March 2019 as part of an action against the regime of Venezuelan President Nicolás Maduro. The announcement said Maduro tried to move $1 billion out of Venezuela via Banco Bandes Uruguay, the Uruguayan subsidiary of Venezuela’s state-owned bank Bandes.
The apps listed their seller as Banco Bandes Uruguay S.A. (with the corporate suffix attached), which is an exact match for how OFAC spells the name.
One of the apps, eBandes, also linked to privacy and support pages on the website bandes.com.uy. A document posted on this website gives Banco Bandes Uruguay’s tax ID as 215395820015. That matches the bank’s ID number listed by OFAC.
According to AppMagic data, eBandes first appeared in the App Store in 2018.
Two apps listed Banco Bandes Uruguay as their developer.
Two apps listed Banco Bandes Uruguay as their developer.
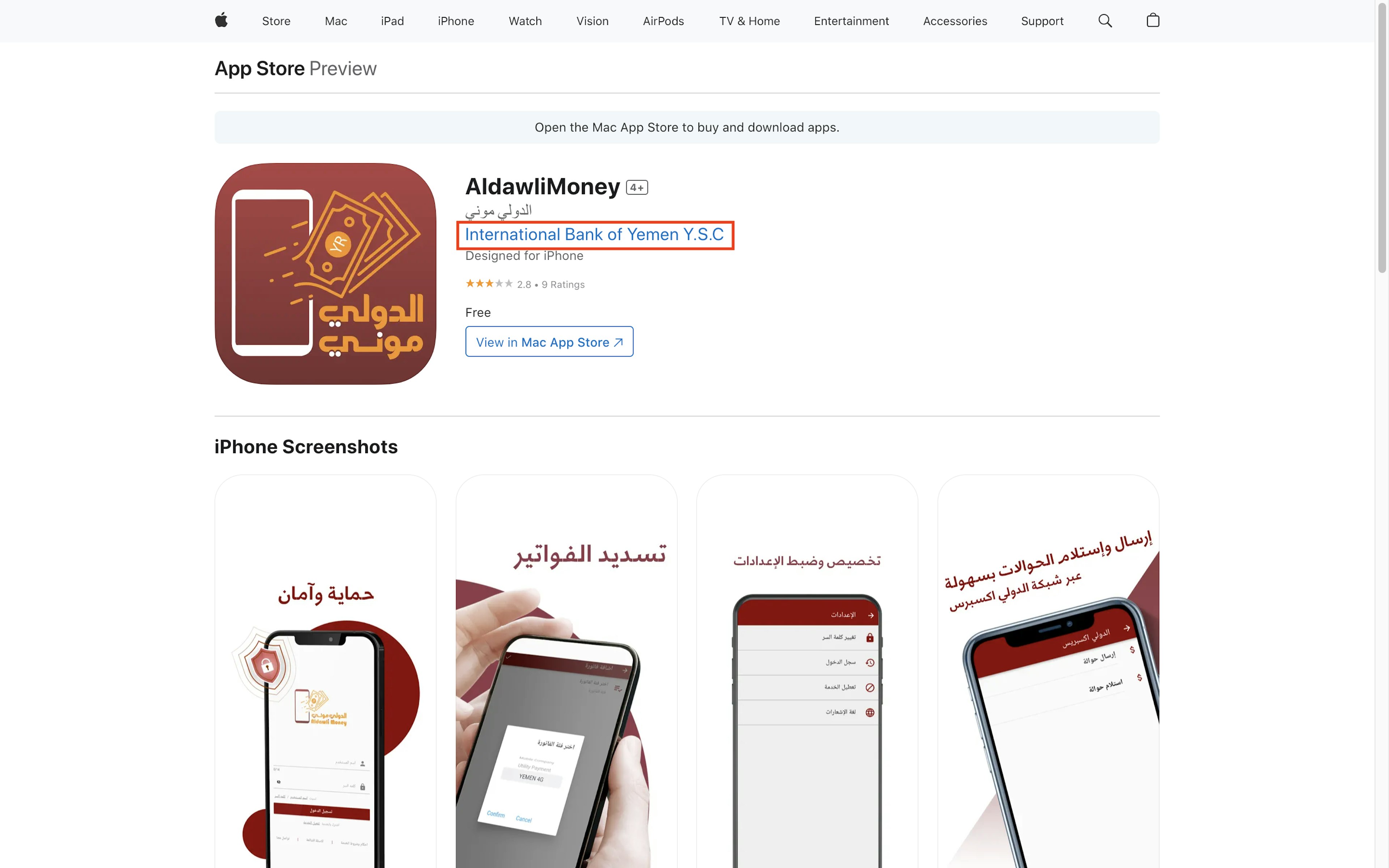
A financial wallet app called AldawliMoney, which was available in the U.S. and Yemen Apple App Stores, listed “International Bank of Yemen Y.S.C” as its developer.
The U.S. Treasury Department announced sanctions against International Bank of Yemen in April 2025, saying it is controlled by Houthi militants. The U.S. said the bank gave the Houthis, a U.S.-designated foreign terrorist organization, access to the SWIFT network for international financial transactions.
The Houthis, who are also under U.S. sanctions, exchanged attacks with Israel and attacked commercial ships in the Red Sea during Israel’s war in Gaza.
The wallet app continued to be available in the App Store for months following the announcement of U.S. sanctions. It is not clear why Apple failed to take immediate action against the app, though a punctuation issue may offer a clue: The app spells the bank’s name without a period after the “C,” a slight difference from OFAC’s spelling.
AppMagic shows the app was last seen in the Google Play Store on April 26, 2025, nine days after the Treasury Department announced sanctions against the International Bank of Yemen.
A wallet app called AldawliMoney listed International Bank of Yemen as its developer. The U.S. sanctioned the bank in April 2025, saying it gave Houthi militants access to the SWIFT network for international financial transactions.
A wallet app called AldawliMoney listed International Bank of Yemen as its developer. The U.S. sanctioned the bank in April 2025, saying it gave Houthi militants access to the SWIFT network for international financial transactions.
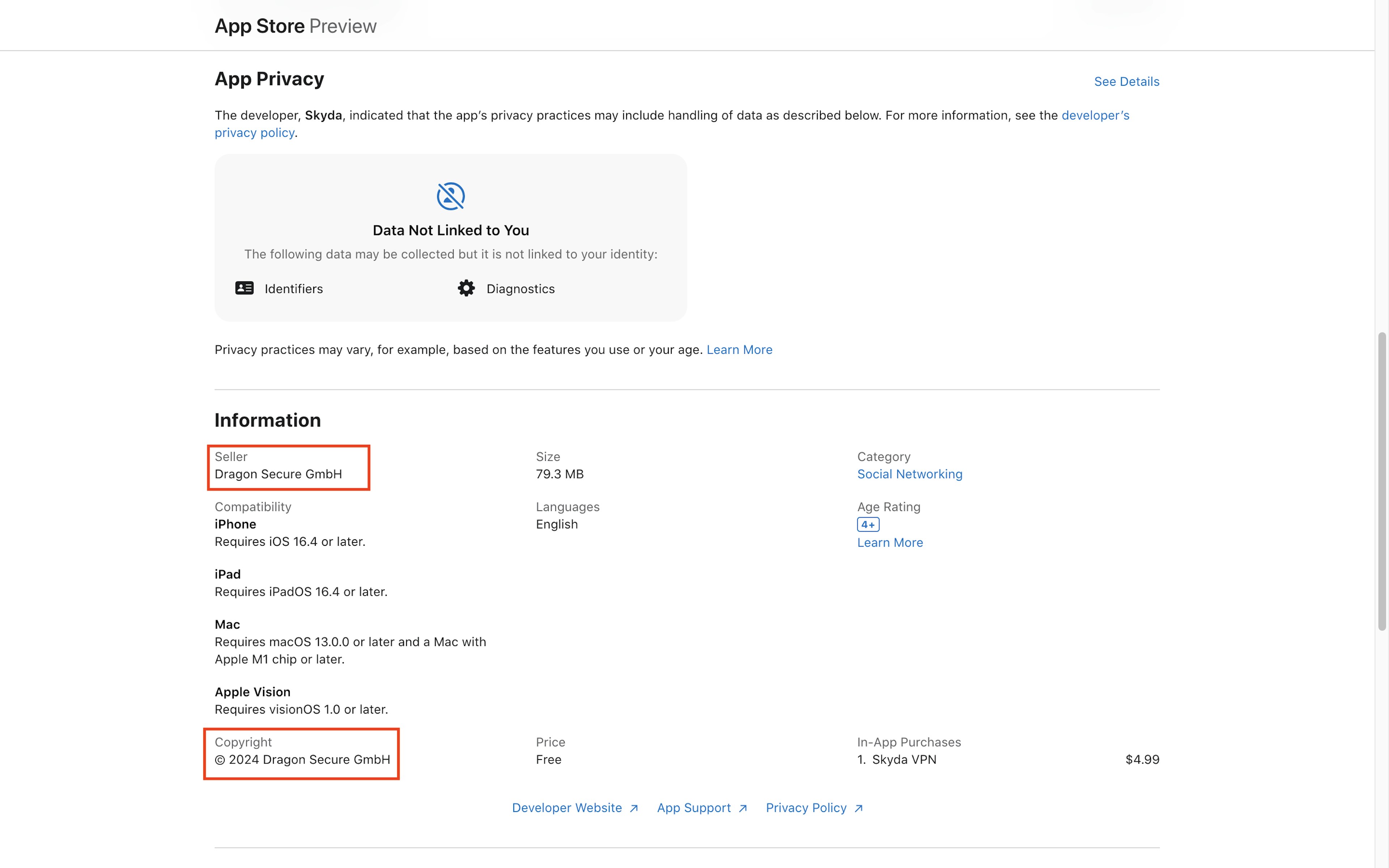
TTP also identified two apps available in the U.S. and Russia Apple App Stores—Skyda - Chats & VPN and Skyda eSIM: Travel Mobile Data—that listed Dragon Secure GmbH as both their seller and copyright holder.
The Treasury Department announced sanctions against Dragon Secure GmbH in December 2024 as part of a broad action against global narcotics traffickers. According to Treasury, Switzerland-based Dragon Secure is majority-owned by a Lithuanian national, Rokas Karpavicius, who is involved in cocaine and methamphetamine trafficking and money laundering.
OFAC identifies the word “Skyda”—the name of both apps—as a known alias of Dragon Secure GmbH. Both apps also linked to a privacy policy page on the website skyda.co, which OFAC says is associated with Dragon Secure. (The website did not load during TTP’s review.)
While the Skyda chat app was free, it charged a fee of $4.99 for VPN service. Because Apple takes a cut of in-app purchases like this, it may have profited from this app beyond the annual developer fee.
Google Play hosted the same two Dragon Secure GmbH apps, but both were last seen there in early January 2025, according to AppMagic.
TTP also identified two apps associated with an accused Lithuanian drug trafficker.
TTP also identified two apps associated with an accused Lithuanian drug trafficker.
TTP’s analysis found that in one case, Apple actually recommended apps for sanctioned entities.
On the App Store page of the previously mentioned Russian banking app Урал ФД СБП (Ural FD SBP), Apple suggested other apps in a “You Might Also Like” section at the bottom. When TTP clicked “See All” to see the full list of recommendations, they included:
- An app from the sanctioned Russian National Standard Bank
- An app from the sanctioned Russian Akibank
- Two apps from the sanctioned Russian Kamkombank, aka Kamsky Commercial Bank
- An app for the sanctioned Russian Bank Accept
- Two additional apps associated with the sanctioned Ural FD bank
Another finding: More than half of the apps identified by TTP (27) had a privacy policy link that either produced an error message or failed to load, and 16 of the apps had the same issue with their support page link. This appears to violate Apple’s requirement that apps provide functional links to support and privacy policy pages and raises further questions about the thoroughness of Apple’s app review process.
Google Play Store
Google says it complies with sanctions enforced by OFAC and requires app developers to do the same. But TTP’s investigation identified a total of 18 apps connected to SDNs in the Google Play Store that evidently escaped Google’s attention.
Eight of the apps had a developer name or information in their description section that matched an SDN, and seven of the apps linked to websites that are clearly associated with SDNs.
All of the apps were connected to sanctioned Russian organizations, including Gazprom, Russia’s state-controlled natural gas giant.
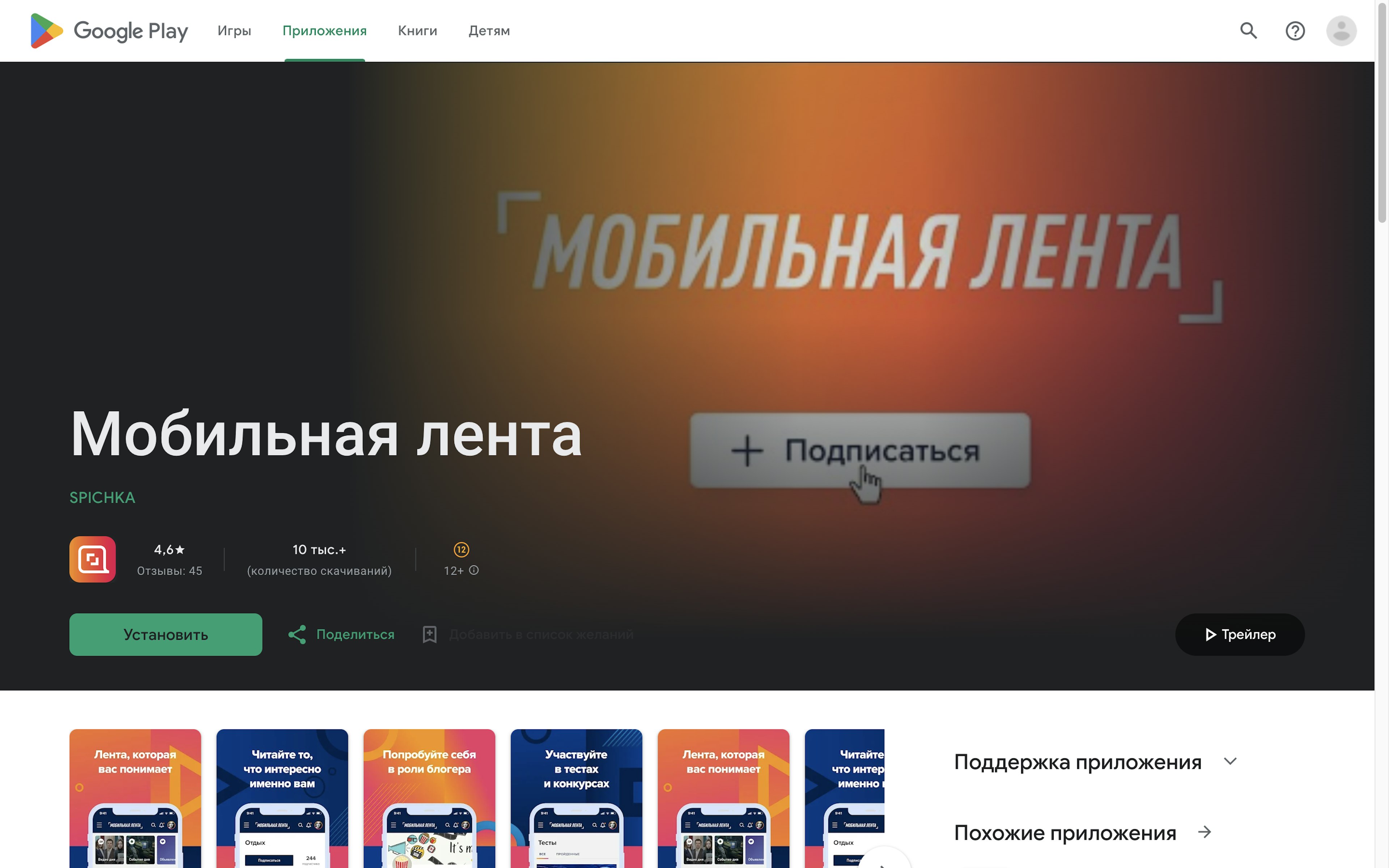
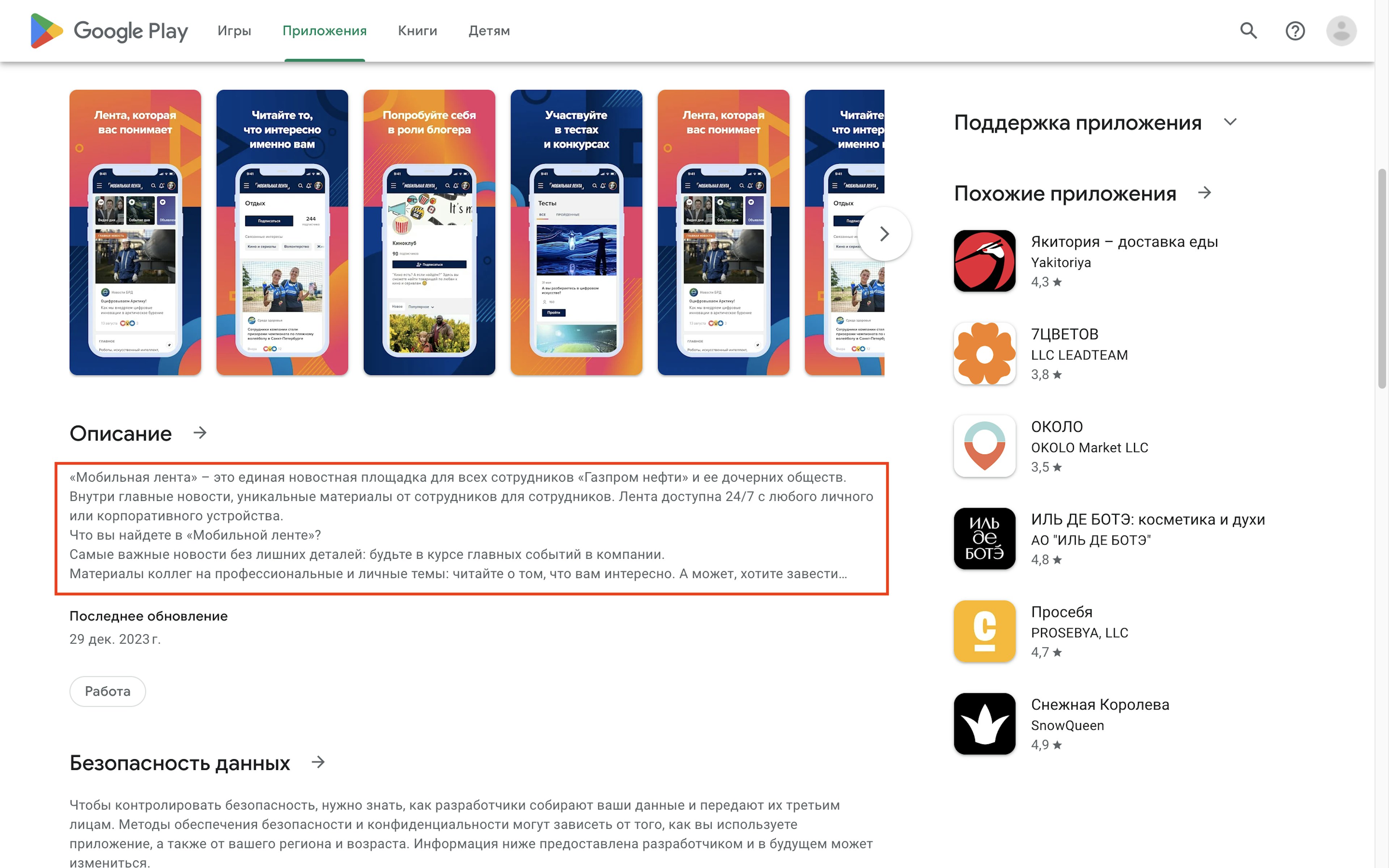
For example, a cluster of four apps showed connections to Gazprom Neft, Gazprom’s oil arm. One of the apps, called Мобильная лента (“Mobile feed) and available in the Russian Google Play Store, described itself as “a single news platform for all employees of Gazprom Neft and its subsidiaries.” The Google Play page for the app indicated it had racked up more than 10,000 downloads.
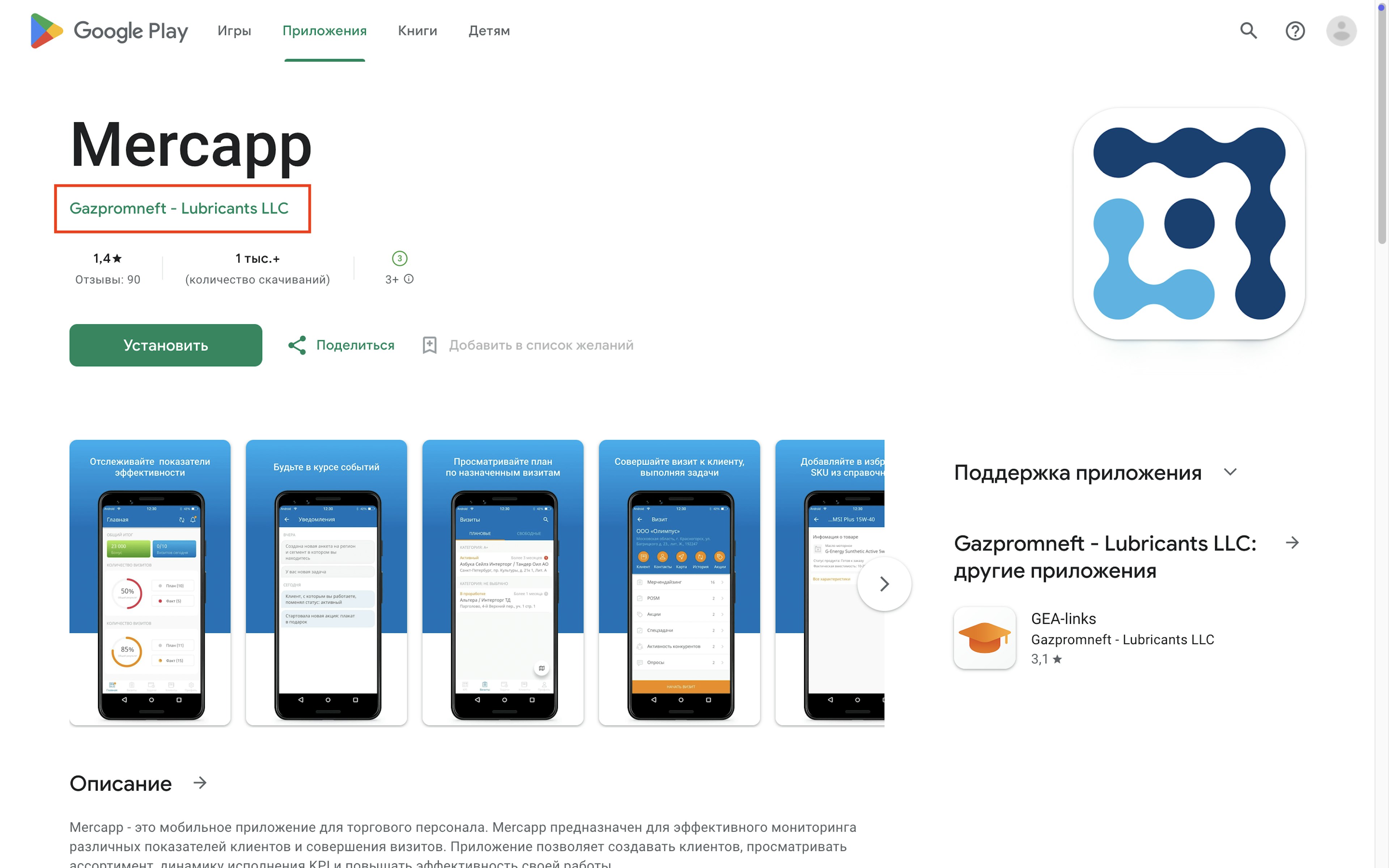
Two other apps—GEA-links and Mercapp—gave their developer as Gazpromneft Lubricants LLC. One was for educating “employees of partner and distribution companies,” and the other was a “mobile app for sales staff.” Both were available in the Russian Google Play Store, and GEA-links was also in the U.S. Play Store.
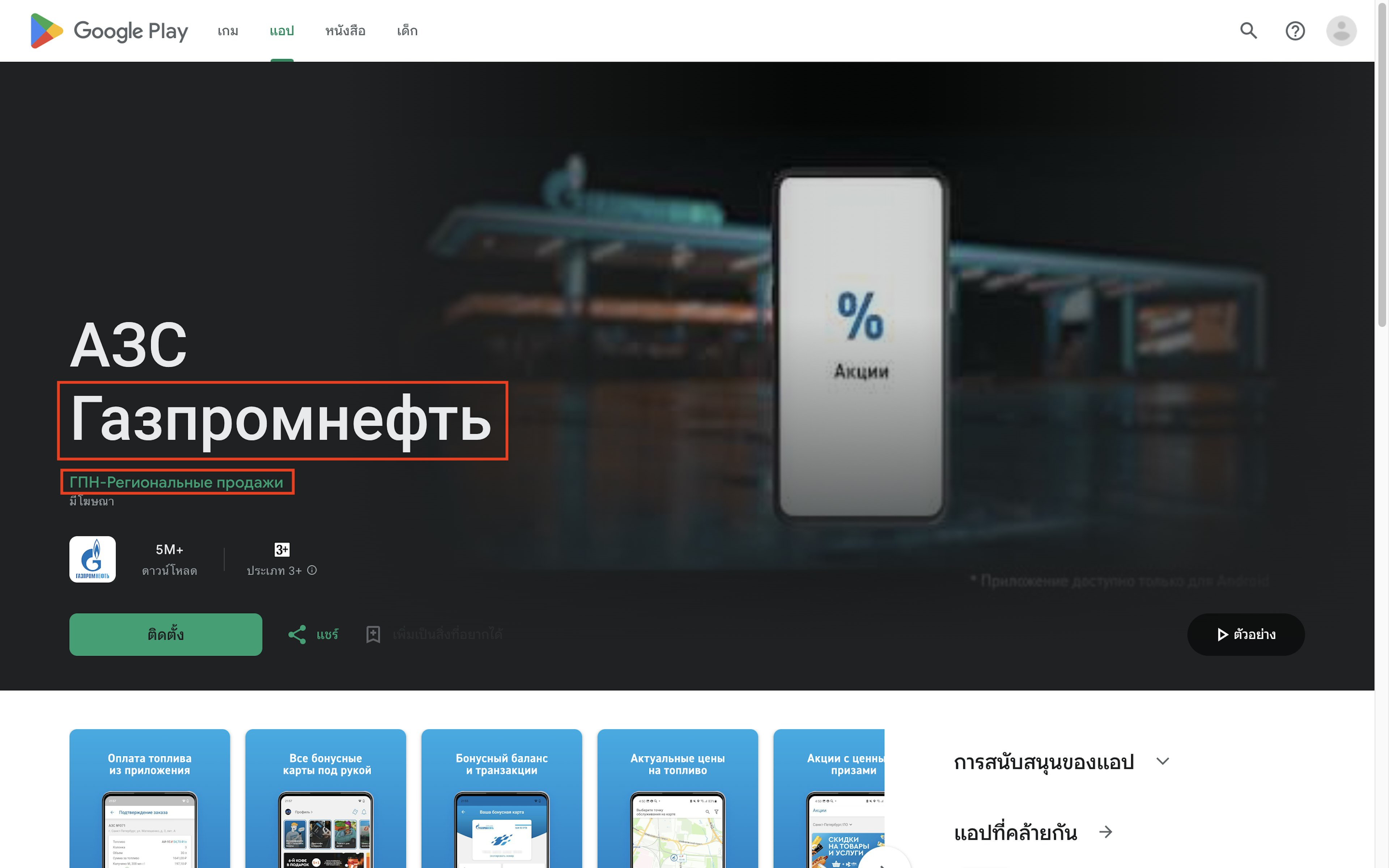
Another app for a “Газпромнефть” (Gazpromneft) gas station loyalty card gave its developer as GAZPROMNEFT-REGIONAL SALES LLC. It was available in the Thailand and Azerbaijan Google Play Stores. (According to the Google Play page, the app includes ads, meaning Google could also be profiting from any advertising that appears on the app.)
The Treasury Department announced sanctions against Gazprom Neft and more than a dozen of its subsidiaries, including the abovementioned Gazpromneft Regional Sales and Gazpromneft Lubricants, in January 2025. The action was aimed at reducing Russian energy revenue used to fund the war in Ukraine.
This app was one of four in the Google Play Store that showed connections to Gazprom Neft, Gazprom’s oil arm which has been sanctioned by the U.S.
This app was one of four in the Google Play Store that showed connections to Gazprom Neft, Gazprom’s oil arm which has been sanctioned by the U.S.
TTP also identified seven Google Play apps associated with Gazprombank, one of Russia’s largest banks which is partially owned by Gazprom.
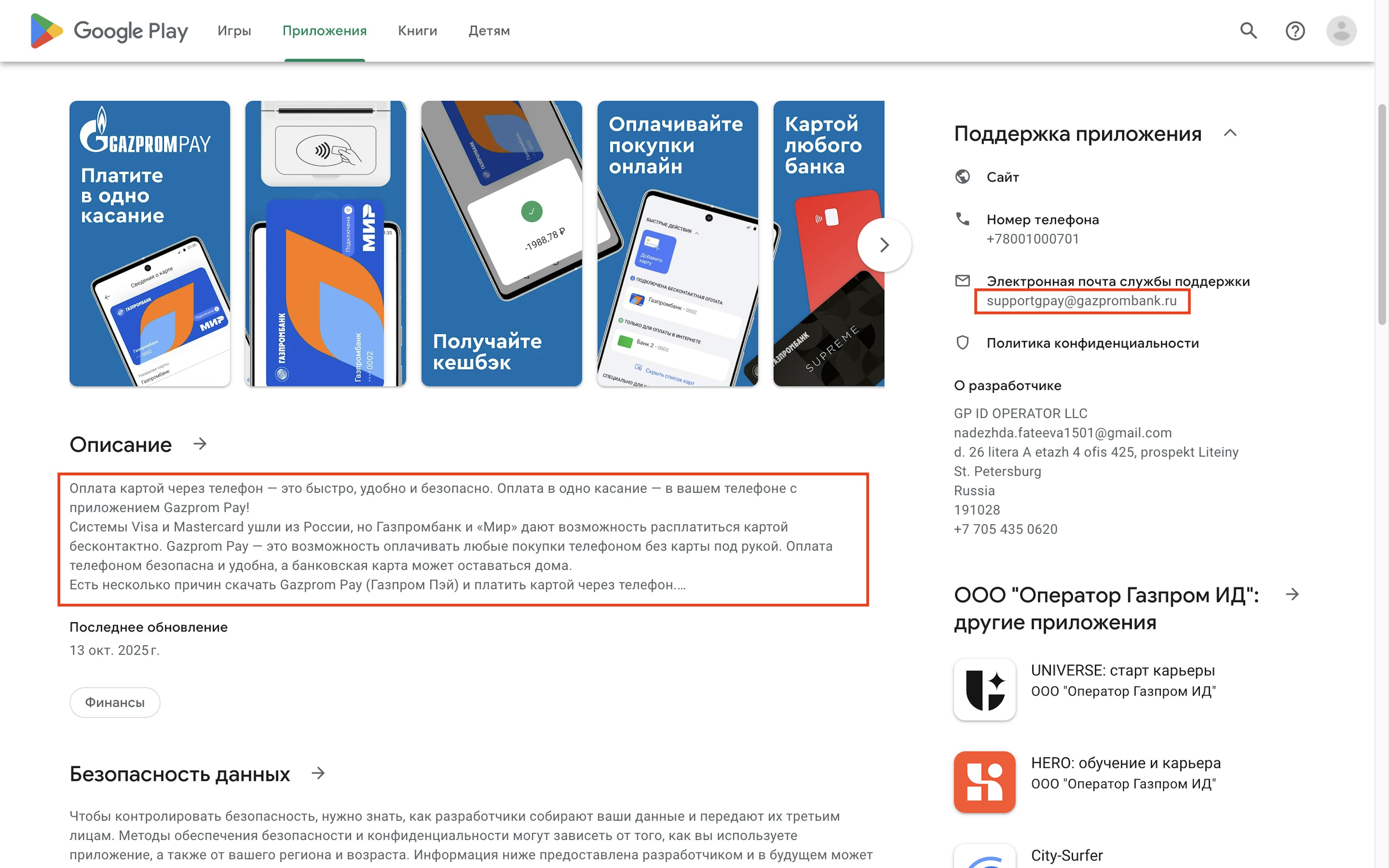
A bank card app called “Gazprom Pay: оплата телефоном” had a Russian-language description that read, “Visa and Mastercard systems have left Russia, but Gazprombank and «Mir» make it possible to pay with a card contactlessly.” The app, available in the Russian Google Play Store, also gave a support email address using the web domain of Gazprombank.
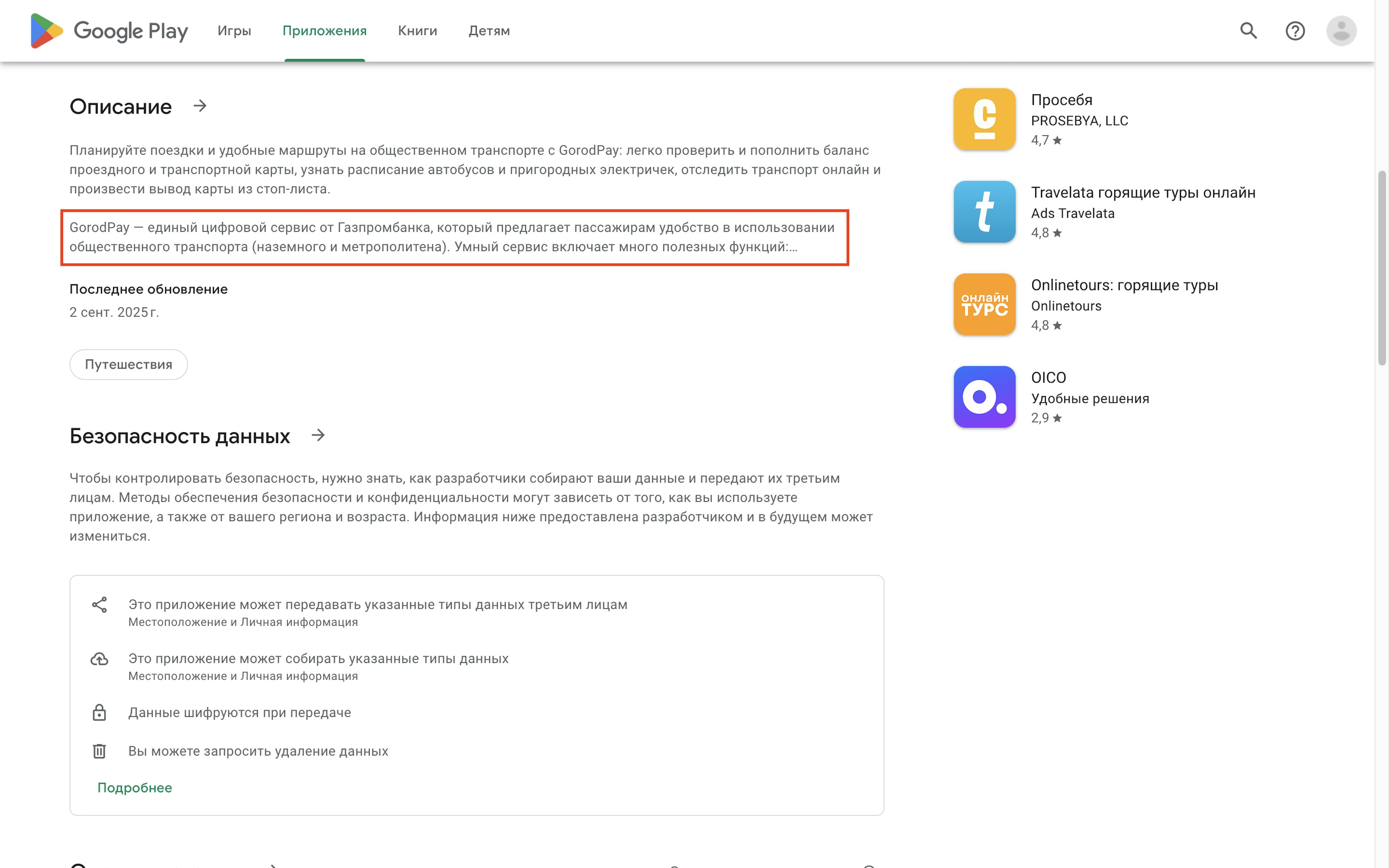
Another app called “GorodPay: транспортный сервис” described itself as a “unified digital service from Gazprombank that offers passengers convenience in using public transport (ground and metro).” The app linked to a website that indicates it is part of “GPB Bank (JSC),” which matches one of the Gazprombank’s aliases listed by OFAC.
GorodPay’s Google Play page shows it has been downloaded more than 1 million times.
OFAC announced sanctions against Gazprombank in November 2024, describing it as a conduit for Russia to purchase military supplies and pay soldiers for its war in Ukraine.
This is one of cluster of Google Play apps associated with U.S.-sanctioned Gazprombank.
This is one of cluster of Google Play apps associated with U.S.-sanctioned Gazprombank.
Below is a table of the 50+ apps identified in the Apple App Store.
Below is a table of apps identified in the Google Play Store.
Note: Updated to reflect additional apps removed from the Apple App Store following publication of this report.